Simplified Operations
Mist portal is now multilingual
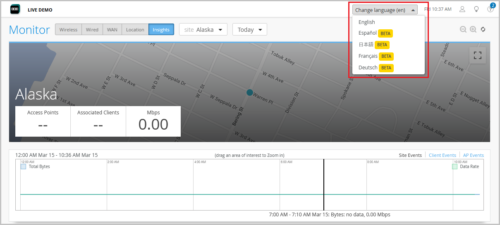
To help users from multiple languages interact more easily with Mist dashboards, we have added localization support to the Mist portal, making it available in multiple languages. At this point, Mist supports the following languages in addition to English:
- Japanese
- German
- French
- Spanish
You can change the language from the Language drop-down list on the Mist portal, as shown below:
Super Observer role
We have introduced a Super Observer role that provides users monitor-only access to the entire organization (all sites), including templates and other pages under the Organization tab. This role serves as an extension of the Observer role which has access only to the site-level pages (to the sites to which they have access) and the inventory and campus fabric pages (if the user has access to all sites). The Super Observer role has the same level of API access as an Observer role.
A user with the Super Observer role does not have access to the Administrators page.
The following is an example of the expanded pages Super Observer has read-only access to under the Organization tab. A Super Observer user can see the admin column pages except the Administrator, as well as the pages under the Access, WAN, Wired, and Wireless columns.
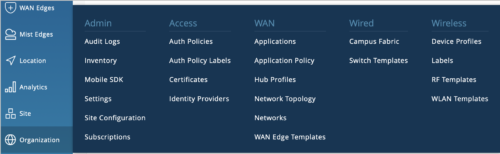
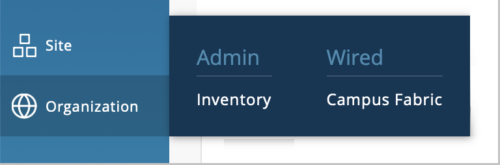
In comparison, the following is what an Observer user has read-only access to under the Organization tab.
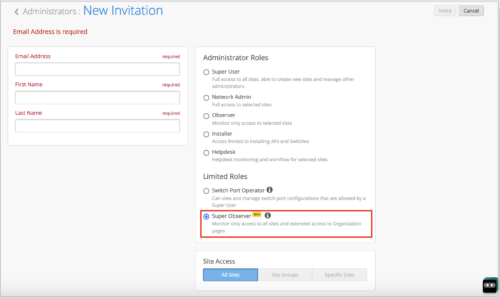
Users with a Super User role can assign the Super Observer role to a user from the New Invitation page (Administrator > Invite Administrators).
New cloud instance for UK
We have introduced a new Mist cloud instance for the United Kingdom. The new cloud instance is named EMEA 02. We have also renamed the existing cloud instance Europe 01 as EMEA 01 on the cloud selection button on the Mist login page. For additional information on Juniper Mist clouds, see Juniper Mist Firewall Ports and IP Addresses for Firewall Configuration.

Option to seek explicit permission of guest portal users to store their personal data
You can now configure the Mist guest portal in such a way that the personal information of users is not stored without their explicit permission. To configure this, select the ‘Opt Out’ as default option on the Customize Layout tab of the custom guest portal configuration page accessed from Mist WLANs. As a result, users accessing the custom guest portal will see the Do not store my personal information option selected by default. They will need to explicitly clear this check box if they want the information they enter into the portal to be stored.
The ‘Opt Out’ as default field is displayed only when you select the Show ‘Opt Out’ field.
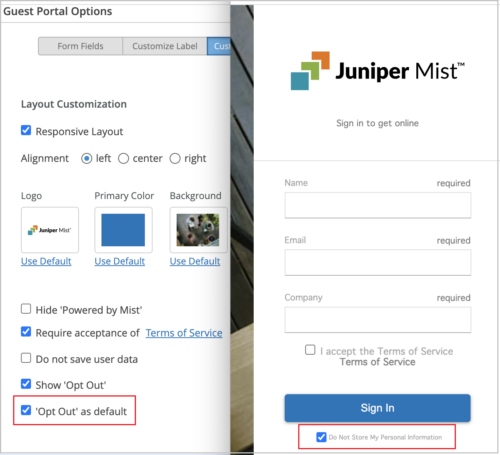
In the image below, the ‘Opt Out’ as default field is selected on the custom guest portal configuration page (on the left), and as a result, the Do not store my personal information option is selected by default on the guest portal login page (on the right). Otherwise, if you configure the Show ‘Opt Out’ option, the user must explicitly check Do not store my personal information when submitting the portal information.
Support for transferring future subscriptions (MSP portal)
The MSP dashboard now allows the admin users to transfer subscriptions with future activation dates from one organization to another. You can transfer subscriptions from the Transfer Subscriptions option on the Organization page on the MSP portal. The Transfer button is enabled when you enter the quantity to be transferred. However, the Transfer button is disabled when the Quantity specified exceeds the Transferable Quantity or the Subscription Quantity.
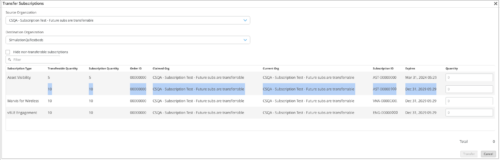
See also: Transfer Subscriptions Between Organizations.
Marvis
Marvis Query Language support for Mist Edges
We have introduced the Marvis Query Language support for Mist Edges. This enhancement enables you to use Marvis Query Language to query Mist Edges and Mist Edge-related events using specific parameters. The following are the Mist Edge-related queries supported by Marvis Query Language:
- List Mist Edges with OOBM IP Address, OOBM MAC Address, Model, Site, or Version.
- List Mist Edge Events with Site, Mist Edge, or Mist Edge Event Type.
- List APs with Mist Edge name/ID and MX Tunnel Status down or up.
- Count Mist Edges with OOBM IP Address, OOBM MAC Address, Model, Site, or Version.
- Count Mist Edge Events with Site, Mist Edge, or Mist Edge Event Type.
- Count APs with Mist Edge name/ID.
- Rank Mist Edges by Tunnel Count.
- Rank Mist Edges by Mist Edge Events Count.
- Rank Mist Edge Event Types by Mist Edge Events Count.
- RANK Mist Edge Version BY Mist Edge Count.
- RANK Mist Edge Model BY Mist Edge Count.
To start the query process, click the Ask a Question link in the upper-right corner of the Marvis page.
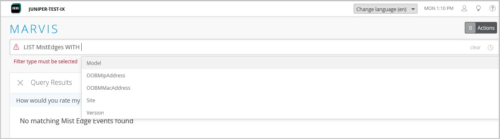
The following image shows how to how to build a Mist Edge query with Marvis Query Language.
Wireless Assurance
WPA3-Enterprise 192-bit security
We have added support for WPA3-Enterprise 192-bit security on the WLAN security. This option offers the highest level of 802.1X security in Wi-Fi by offering GCMP-256 Encryption over the air and requiring more secure certificates. You configure it just like you would configure WPA3-Enterprise under a Site or Template WLAN in the Security section. You then check the “Enabled 192-bit Encryption” checkbox.
Note that there is no transition mode and no 802.11r fast roaming with WPA3-Enterprise 192-bit.
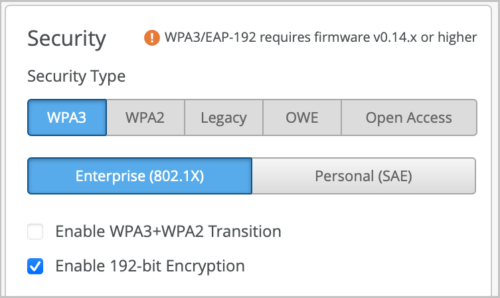
There are some RADIUS side requirements to leverage WPA3-Enterprise 192-bit. EAP-TLS must be used. The 192-bit mode only supports certificate authentication with restrictions around the allowed EAP ciphers. Mist Access Assurance supports EAP-TLS authentications when WPA3-Enterprise 192-bit is used.
Permitted EAP cipher suites for use with WPA3-Enterprise 192-bit mode are:
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
WPA3-Enterprise 192-bit requires AP Firmware version 0.14.29091 or newer. Most of the recent clients support WPA3-Enterprise 192-bit, but it is our recommendation to default to WPA3-Enterprise and leverage this WPA3-Enterprise 192-bit in environments that need higher security and where you have verified device support. The downside of this security mode is there is currently no fast roaming with 802.11r.
Client VLAN policy override on APs
You can now set up WxLAN policies to override client VLANs. The intended use case is for supporting per site VLAN flexibility with mPSK. That is Site A can use VLAN A for PSK A and VLAN B for PSK B and Site X can use VLAN X for PSK A and VLAN Y for PSK B. You can use the WxLAN policies to assign VLANs to clients based on the PSK role using AAA attribute User Group label. The WxLAN-driven VLANs override any other VLAN assignments on a client, for example, a dynamic VLAN received from RADIUS.
For this feature to work, you must ensure that the VLAN that is planned to be assigned via a WxLAN policy is already present in WLAN configuration.
To enable this feature, follow the below steps:
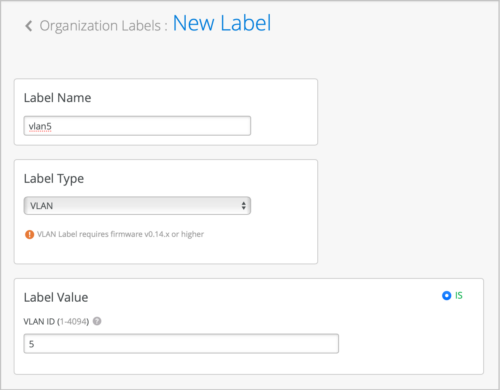
- Configure a WxLAN policy label with Label Type VLAN (Organization/Site > Labels > Add Label). You must specify a VLAN ID in this configuration. If you create an Org Label, you can use a VLAN variable in {{*}} format and resolve the variable at the site level or device profile level.
![]()
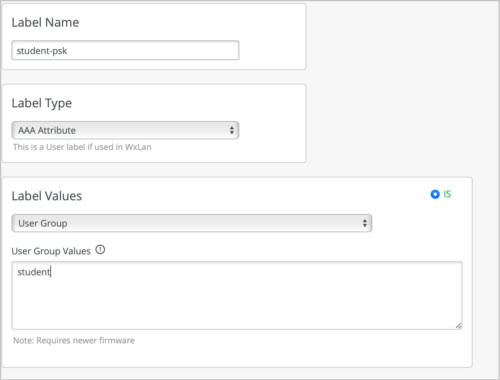
- Create an AAA Attribute user group label to match the PSK role. You can also create a client label, but it is suggested to use AAA Attribute at scale.
![]()
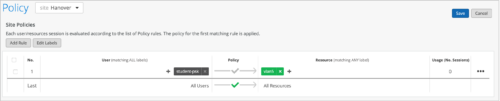
- Create a WxLAN policy by including this VLAN label in the Resources field (Organization > WLAN Templates > Policy or Site > Policy > Add Rule). The policy assigns the matching users to the specified VLAN.
![]()
This feature can be used in addition to the normal methods of assigning a user to a VLAN by policy such as through RADIUS AVPs (Tunnel-Private-GroupId or Airespace-Interface-Name) or VLAN attached to mPSK. Use of VLAN policy override requires AP firmware version 0.14.29091 or newer.
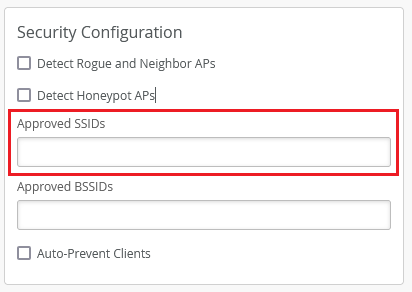
Support for approving wildcard SSIDs
The Approved SSID field under the Security Configuration in site settings (Organization > Site Configuration) is used to exclude specified SSIDs from rogue and honeypot detection. This field now supports the use of wildcards and partial match. For instance, to approve an SSID named DIRECT-roku-755-22DDFF, you can include only the text direct* in the Approved list so that all SSIDs starting with the word direct get approved. This feature is useful when there may be many SSIDs with the same SSID name structure, for example, printers or TVs with Wi-Fi Direct. Partial BSSID matching is already supported in Approved BSSIDs, for example (“cc-73-*”, “cc:82:*”).
Wired Assurance
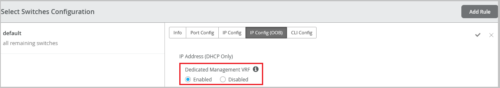
Dedicated management VRF instance for switches (out of band)
You can enable a dedicated management virtual routing and forwarding (VRF) instance on switches. Enabling this feature confines the management interface (em0/me0/fxp0,vme) to a non-default VRF instance. This feature works for standalone devices and Virtual Chassis systems running Junos OS version 21.4 or later. With the dedicated management VRF instance in place, management traffic does not have to share a routing table with other control traffic or protocol traffic.
By default, out-of-band management traffic is not clearly separated from in-band protocol control traffic in switches. All traffic passes through the default routing instance and shares the default inet.0 routing table.
You can configure dedicated management VRF from the IP Config (OOB) tab in the Select Switches Configuration section on the organization-level or site-level switch templates (Organization > Switch Templates or Sites > Switch Configuration). You can also do this from the switch details page (Switches > Switch Name).
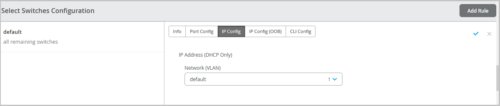
In-band management network at the switch template level
The switch templates now provide the option to configure networks for in-band management traffic. You can do this from the IP Config tab in the Select Switches Configuration section on the organization-level or site-level switch templates (Organization > Switch Templates or Sites > Switch Configuration). This configuration option is already available at the switch level (Switches > Switch Name).
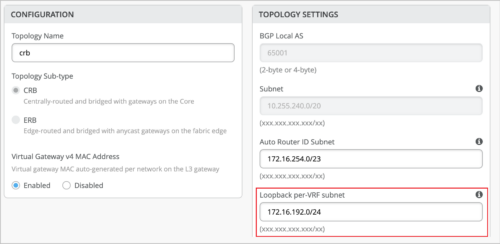
Update to Loopback per-VRF subnet requirement
You can now use a /19 or smaller subnet in the Loopback per-VRF subnet field, which is part of Juniper Mist campus fabric configuration (Core-Distribution and IP Clos topologies). Previously only the /19 subnet was allowed. Also, for new topologies, we have changed the default Loopback per-VRF subnet value from 172.16.192.0/19 to 172.16.192.0/24. This does not apply to the existing topologies. Mist uses this subnet to automatically configure loopback interfaces (lo0.x) per VRF instance that is used for services such as DHCP relay.
Pods configuration for site-level campus fabric topologies
We have improved the scalability of site-level campus fabric topologies with the support of pods. Pods allow you to group your access and distribution devices in a campus fabric topology. A pod could represent a building. For example, you can create a pod for each of the buildings in your site and create connections between the access and the distribution devices in that pod. You do not have to connect the same set of access devices to the distribution devices across multiple buildings.
Pods configuration is available for the following topology types:
- Campus Fabric Core-Distribution
- Campus Fabric IP Clos
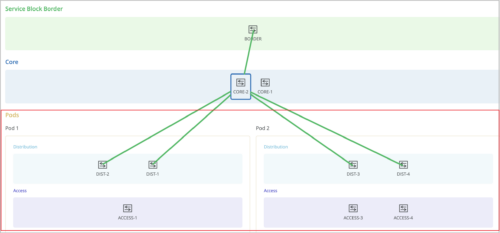
Dynamic VLAN assignment on ports with 802.1X authentication
Switch ports configured with 802.1X authentication support dynamic VLAN assignment.
During authentication, the RADIUS server may return a VLAN attribute (Tunnel-Private-Group-ID or Egress-VLAN-Name) in the RADIUS access-accept message. This attribute is then mapped to the VLANs configured on the switch port to perform dynamic VLAN assignment. To enable a port to perform dynamic VLAN assignment, you can configure these VLANs (which will be returned by the radius server) using the port profile. This is an optional configuration. For an IP Clos topology, you must fill the dynamic VLAN field so that the corresponding VLAN definitions are pushed to the switch.
To configure the dynamically returned VLAN:
- Navigate to the Port Profile configuration section on the switch template or switch details page (Organization > Switch Templates > Template Name or Switches > Switch Name).
- Select the Use dot1x authentication check box.
- Select the Dynamic VLAN check box.
- From the Networks drop-down list, select the VLANs that you want to include in the VLAN pool.
- After saving the port profile, assign it to the switch port on which you want to configure the dynamic VLAN assignment feature.
IP Clos deployments with dedicated border nodes can now function with one core switch
For IP Clos campus fabric deployments that use dedicated switches (border nodes) to run the service block functionality, we have reduced the minimum number of core switches required from two to one switch.
This change does not apply to the deployments where the core switches are configured to carry out the service block functionality as well.
In a campus fabric topology, border nodes connect to external devices such as firewalls, routers, or critical devices. External services or devices (for example, DHCP and RADIUS servers) connect to the campus fabric through border nodes.
Transceiver column in Port List
The Port List on the switch details page now indicates whether the transceivers used in the switch are Juniper-supported or not. A new column named Transceiver shows this information. This column has the following values:
- Juniper: Indicates that the transceiver is supported by Juniper.
- Non-Juniper: Indicates that the transceiver is not supported by Juniper.
WAN Assurance
OSPF support for WAN Edge devices
Mist supports configuration of Open Shortest Path First (OSPF) on WAN Edge devices. OSPF is a link-state routing protocol used to determine the best path for forwarding IP packets within an IP network. OSPF divides a network into areas to improve scalability and control the flow of routing information.
You can configure OSPF from the Routing section on WAN Edge templates (Organization > WAN Edge Templates), hub profiles (Organization > Hub Profiles), or the WAN Edge device configuration page (WAN Edges > WAN Edges > WAN Edge Name).
OSPF configuration involves the following two steps:
- Defining an OSPF area from the OSPF AREAS tile.
- Applying that to the WAN Edge device from the OSPF CONFIGURATION tile.
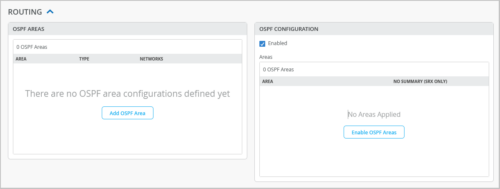
For more information about OSPF areas, see this Junos documentation: Configuring OSPF Areas.
VRF route leaking
Mist WAN Edge devices support VRF route leaking, a feature which enables you to share route information across VRF instances. This feature allows you to share traffic across VRF instances within a device or between multiple devices.
To configure VRF route leaking on an SSR device:
- On the SSR device, create a routing policy for the route (prefix) to be shared and include the target VRF in it. Typically, this policy is associated with a hub (in a hub-to-spoke use case). You can do this from WAN Edge templates, hub profiles, or individual WAN Edge devices.
- On the hub device, configure an application policy with the route (the prefix included in the routing policy) specified in the destination field. Note that the spoke device requires an application policy only if there is no appropriate BGP policy between the spoke and the switch connected to it.
For a WAN Edge SRX device, route leaking is part of the Mist intent configuration model and can be enabled through application policies.
Support for testing your WAN link speed (SSR)
Mist provides an option to test the speed of WAN links on the Session Smart Routers (SSRs) managed by Mist. This feature supports specific use cases. For example, you can test the speed of circuits installed to a branch office with an SSR at the edge of the customer premises. You can carry out tasks such as the following:
- New link qualification
- On-demand speed tests when a low link speed is suspected to be causing link issues
You can run speed test from the SSR WAN Edge details page (WAN Edges > WAN Edges > WAN Edge Name) and then select the WAN port from the port panel. Results for past on-demand or scheduled speed test runs will be available on the WAN Edge details page.
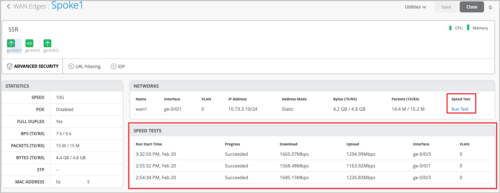
Before running the test, ensure that the WAN link has connectivity to the Internet, where the speed test infrastructure can be reached. For SSR clusters, the speed test can be run only on the active WAN link. The speed test feature does not require any firmware version update for your SSR.
Support for disabling WAN Edge ports
If you want to disable a LAN port or WAN port on a WAN Edge device for any reason, you can do so from the WAN Edge template (Organization > WAN Edge Templates) or from the WAN Edge configuration page (WAN Edges > WAN Edges > WAN Edge Name). To administratively disable a WAN Edge device port, select the Disabled check box under the specified interface on the LAN or WAN configuration section.
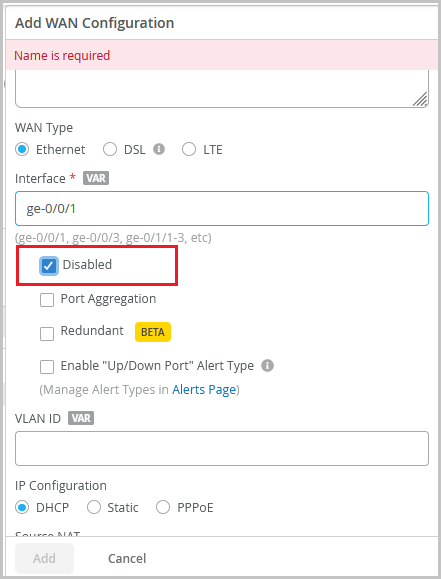
This option is part of interface configuration. If you use this option to disable an aggregated Ethernet (AE) interface or redundant Ethernet (reth) interface, all member links are disabled.
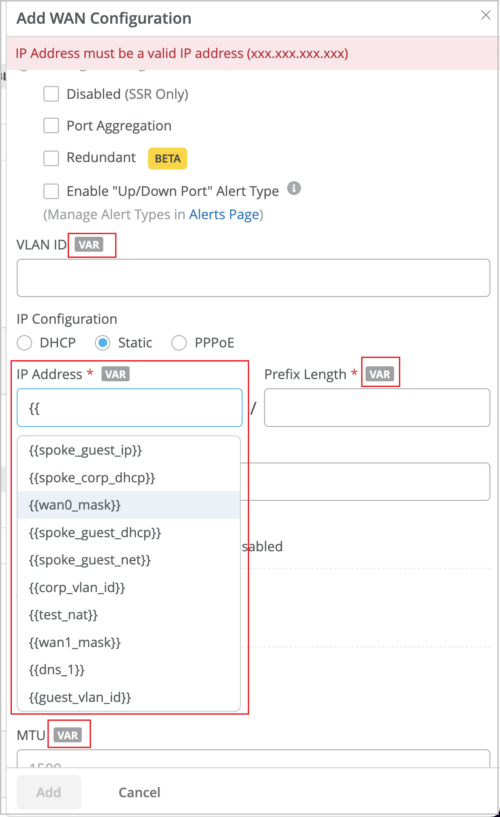
Hint text for fields that support site variables
The WAN Edge configuration fields that support site variables now come with a VAR label. This label helps you quickly identify the fields which can be configured using site variables. Also, the fields with this label will display the matching variables (if configured) as you start typing a specific variable in it. To know more about site variables, see Configure Site Variables.
Behavior Changes
Updates to user privilege inheritance at the site level
We plan to update the workflow for resolving user roles (privileges), effective after May 3, 2024. With this update, the role derived to the user maps to highest granted privilege at the scope (MSP, organization, site). Today this is already the case for MSP vs organization. The implementation will become consistent for organization vs site as well. It is the same behavior for local and SSO users.
Therefore, an organization level role could override an explicit site-level role. For example, if a user is granted Super User role at the organization level and Helpdesk role at the site level, the Super User role takes effect at the site level.
Note: Configuring multiple organization and site privileges is not allowed in the Mist portal, but it is allowed in the API.
User role assignment at the site level
| Role granted at Organization 1 | Role granted at Site 1 | Resultant role at Site 1 | |
| Behavior till May 7, 2024 | Super User | Helpdesk | Helpdesk |
| Behavior from May 7, 2024 | Super User | Helpdesk | Super User |
Changes to /self API (for MSP users)
Starting from May 7, 2024, the /self API query fetches only the explicitly granted privileges for an MSP user. It does not fetch the inherited privileges of the user. To view the inherited privileges at the organization level, you need to run the GET API query ‘/msps/:msp_id/orgs’ at the MSP level. To view the inherited privileges at the site level, run the GET API query (/orgs/:org_id/sites) at the organization level.
Feature Deprecation
Webhook topic asset-raw to be deprecated
We will deprecate the webhook topic asset-raw from 06/30/2024 onwards. It is replaced with a new topic named asset-raw-rssi. See the Webhooks section in https://api.mist.com/api/v1/docs/Site#webhooks.
The post March 29th 2024 Updates appeared first on Mist.